j-j.co.za
Sharing thoughts and ideas on business, security and photographyGoogle acquisition trail Feb 2001 – Aug 2010 #in
Posted on August 26, 2010This is a rather impressive info graphic put together by scores.org laying out the timeline of Google acquisitions from Feb 2001 to current. Take a look through, a walk down memory lane 🙂
The acquisitions are categorised (left to right) according to the revenue intent behind the acquisition, into either revenue growth, competition reduction, or a bit of both.
The inner circle is a colour coded pie chart reflecting whether the key asset obtained through the acquisition was People (yellow), Market (red) or Technology (blue).
The sizes of the outer circles also shows the relative size of the acquisitions. The relative sizes don’t take into account the size of Google at the time of the acquisition nor inflation so take care before reading too much into these sizes.
The list is quite comprehensive although it is not believed to be complete, the author has indicated the graphic will be updated to reflect corrections.
Click through to see the full infographic (It is extremely long so isn’t included here on the front page).
2010 Data Breach Investigation Report – Who stole my client’s cheese? #in
Posted on August 25, 2010The first-ever joint report by the Verizon Business Risk data crime investigation team and the U.S. Secret Service presents a fascinating and current insight into the murky world of data theft and cyber crime. Contrary to general expectations 85% of all stolen data records can be traced back to organised crime. Woaah. While almost 50% of cases had active insider involvement, these were small-time jobs resulting in only 3% of records lost. So yes, watch out for your employees, but beware of those syndicates!
Read more in Woody Leonhard’s summation of the report here.
Download a copy of the VBR/USSS report from Verizon Business here
Howto : Small Business IT Governance Implementation #in
Posted on August 25, 2010One of the key challenges of IT governance is how to break it up and make it understandable and implementable for small businesses. Cost/benefit is always a key challenge and unless there is a practical sensible way that adds value to the business then IT governance is not going to work in small business.
ISACA have released a nicely put together article in their J-Online section of the website. Small Business IT Governance Implementation by Janeane Leyer and Katelyn Quigley provides useful practical advice on how to implement. In doing so the article provides three key questions in a simple framework and discusses six critical success factors for the implementation.
Abstract
The largest risks to businesses today are failure to align information technology to real business needs and failure to use information technology to create value for the business. Effectively managed IT can provide small businesses with a competitive advantage, whereas ineffective management can impair the business as a whole. With recent increases in demand for cost reduction, the need for small businesses to actively manage their IT resources has never been greater.
This article will provide an overview of IT governance, discuss the benefits to small businesses, suggest a framework for implementation in small businesses and discuss critical success factors.
ISACA Whitepaper “Securing Mobile Devices” #in
Posted on August 25, 2010ISACA have released a whitepaper on the securing of mobile devices. This is the first in a series of documents which will eventually include audit/assurance programs for such devices. The overview of these documents can be found here.
Abstract of white paper
Mobile computing devices have become a critical tool in today’s networked world. Enterprises and individuals alike rely on mobile devices to remain reachable when away from the office or home. While mobile devices such as smartphones, laptops, personal digital assistants (PDAs) and Universal Serial Bus (USB) memory sticks have facilitated increased convenience for individuals as well as the potential for increased productivity in the workplace, these benefits are not without risks. Mobile devices have been, and continue to be, a source of various types of security incidents. These stem from issues such as device loss, malware and external breaches. As the availability of human resources and systems continues to be critical to society and business operations, it stands to reason that mobile device usage will continue to escalate as will the features that these devices offer. It is therefore imperative that proper risk management be applied and security controls implemented to maximize the benefits while minimizing the risks associated with such devices.
Securitysearch.co.uk writeup on the whitepaper here.
ISACA SA Chapter meetings in October (Dbn, Jhb, Pta) #in
Posted on August 25, 2010Three of the ISACA chapters are having meetings in October. Details are below and will be updated as confirmation of speakers is obtained. Don’t forget the #isaca2010 conference in September.
KZN regional chapter meeting
- Date : 7 October 2010
- Venue : PKF Offices in Umhlanga
- Topic : To be confirmed
Pretoria regional chapter meeting
- Date : 14 October 2010
- Venue : To be confirmed
- Topic : To be confirmed
Johannesburg regional chapter meeting
- Date : 26 October 2010
- Venue : To be confirmed
- Topic : To be confirmed
Confirmation of attendance
As always, please confirm your attendance with Nadine on 011-803 0803 or admin@isaca.org.za a few days ahead of time.
163 Megapixel panorama : View from my lounge
Posted on August 22, 2010This morning I created and uploaded my Gautrain panorama (see previous post). That encouraged me to try and make a more detailed and refined panorama using a better camera. I have always enjoyed the view from my lounge / balcony so decided to try and create a panorama shot from there.
Using a basic tripod and a Canon EOS 550d DSLR camera I took a series of 31 photos which were then run through Microsoft ICE and uploaded to Photosynth. The resulting image is the 163 megapixel panorama image present below. What is really impressive is the level of detail present in the synth. Try zooming into leaves on some of the trees, cars on the freeway in the distance or to windows on the office block. This really is powerful technology which anybody can enjoy.
This second synth was taken over lunch using my Nokia E71. The quality isn’t great as it was taken handheld. The synth has many gaps and misplaced photos. I took 77 photos and ICE used 66 of them to give a 360 degree vertical coverage and 144 degrees horizontal. I uploaded it out of interest thinking it would be a bit of a disaster but after playing with it for a while made it public and added some highlights. Its amusing to play with for a short while.
You can download the Microsoft ICE tool here at the Microsoft Research website.
Gautrain station photo synth (3d image composite)
Posted on August 21, 2010Below is a very “rough and ready” photosynth of the Gautrain station platform in Sandton. It was created from 35 photos taken handheld on my Blackberry Bold 9000 (without flash) the other day while waiting 10m for the train to arrive.
The synth was put together with Microsoft Image Composite Editor (MS ICE) and the Microsoft Photosynth plugin for it. All free software that does quite an amazing job of stitching together a bunch of randomly ordered photos that you drag into the window. I will add some more screenshots and information in another post later. In the meantime here is the synth.
Excuse the gaps (in pics) and occasional mismatch, I did move forward at one stage to avoid getting too many people in on the platform to the right, and this caused a little bit of a mismatch with the railway line.
I’m very impressed by what can be achieved with such a low end “camera” and some very nifty software from Microsoft. I am very attempted to take along the DSLR and tripod next time to see how that would come out. Comments and feedback welcome.
Click on the picture below to “activate” the synth then expand to full screen and move the view around to enjoy the full 3d effect.
Standard Bank phishing attacks
Posted on August 16, 2010Over the last few weeks I have been getting emails “from” Standard Bank on a regular basis, probably one or two a week. Today I received two more. I am not a Standard Bank customer, so it is immediately obvious that they must be fake. Perhaps a little less so for those who bank with Standard Bank? Both of these mails look a little different, originate from different email addresses, and have slightly different profiles. Standard Bank (or someone) is on the ball (thankfully) as when I tried to follow up on the mails to see how the attacks were working both had been blacklisted with Firefox/Mozilla as phishing sites, and the offending pages had also been removed. There was one a few weeks back that had not yet been blocked at the time I tried to access it, so I have a little more info on that attack, which I will post as an update when I get a chance (probably on only the weekend).
Update on Oracle password hashes and crackers #in
Posted on August 16, 2010As mentioned in my very first post on this “new and improved’ site, my original site from way back when had some information on Oracle password hashes and a list of default passwords. This initial work was taken and improved on by Marcel-Jan Krijgsman and subsequently Pete Finnigan (read more about it here), who now runs what is probably one of the best Oracle Security resources available on the net.
During those early days not much was known about Oracle password hashes. There also weren’t too many options when it came to cracking them. Adam Martin came up with a plan in the early days, writing some code that would take create an account, and then change the password to each word in a dictionary (stored in another table) using the oracle password change functionality, and then grab the hash after the change to compare it to the hash you are trying to crack. It was slow (around 10 passwords/second if I recall correctly). I wrote my own version to automate the process and build a “pot” of known hashes along the way. I was busy getting this ready for release when Orm released his far superior tool. At that stage I stopped development and released my list of known hashes.
Orm’s tool was orabf. This tool changed the game, as it was a completely offline tool not needing a running database and it was orders of magnitude quicker. It is probably still the best password cracker around for pre 11g hashes. The early version was a little buggy after a few mails Orm quickly fixed it and has improved it since then. (History here). Download orabf here.
A little about Oracle password hashes and the algorithm (Oracle 7- Oracle 10g)
Passwords can be up to 30 characters in length. The username and password are concatenated and all characters are converted to uppercase, then an eight byte hash is generated using the DES encryption algorithm without any salt (just the username).
The hashes can be obtained using either
* SELECT username, password FROM DBA_USERS;
* SELECT name,password FROM SYS.USER$ WHERE password is not null;
The second is potentially safer if there is a suspicion the server may have been compromised.
Use orabf (download as per link earlier) to crack these hashes, or get the modified version of John the Ripper.
Oracle 11g pasword hashes
Oracle 11g password can be up to 50 characters in length, and passwords are no longer case insensitive. The passwords are stored in two ways (Ala LANMAN hashes – don’t they learn from mistakes of others?), the old style DES (password field) AND the new SHA-1 (spare4 field).
Oracle 11g concatenates the password and salt, then applies SHA-1 to obtain the hash.
Password hashes can no longer be selected from dba_users, so can only be obtained as follows :
* SELECT name,spare4 FROM SYS.USER$ WHERE password is not null;
For more detail on the the Oracle 11g password hashing read the writeup at Recurity Labs.
To crack Oracle 11g hashes you can use The Hackers Choice (THC) OrakelCrakert which handles both brute force and dictionary attacks. Check first though to see if the old-style hashes are available first, as it’s much easier to crack the new style password if the old style is known first, THC explain how this works in their post linked above.
That’s pretty much where things are at currently with Oracle passwords and hashes. There are many more tools out there to help with hacking and securing Oracle. Google is your friend 🙂
Upcoming ISACA chapter meetings in East London and Jhb #in
Posted on August 13, 2010There are two chapter meetings coming up in East London and Johannesburg in the next few days. Hope to see lots of people there. I personally hope to attend the Jhb meeting, travel plans allowing.
Date: 18 August 2010 at 2:30 pm
Venue: PricewaterhouseCoopers , Palm Square office park , Acacia House , Bonza Bay Rd , Beacon Bay
1) Andrew William Mpofu will be presenting: “Information Security as a strategic business asset”
2) Chris Knox will be presenting: “Information Security Risk Assessment methodologies”
3) Networking & Refreshments
Date : 24 August 2010 5pm Registration with the event starting at 5:30pm
Venue : PriceWaterhouseCoopers offices in Sunninghill, Johannesburg
1) Jason Gottschalk will be presenting on “Access Governance – The precursor to Identity and Access Management”.
2) Gerhard Hechter, PKF will be presenting on “Taking risks cleverly / Business intelligence”
Attendance
To confirm attendance to either of these meetings please contact Nadine on 011-8030803 or admin@isaca.org.za
Congratulations
Lastly, congratulations to all those who wrote and passed CISA, CISM and CISSP. I believe results for all 3 were released today.
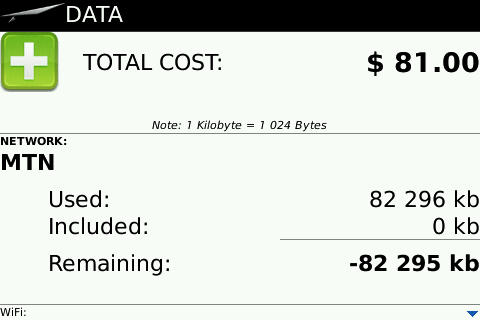
Followup on Blackberry Data Useage in South Africa #in
Posted on August 13, 2010Following up on my post around Blackberry data useage found here.
It has now been a week of monitoring my data useage on my Blackberry Bold 9000. Details around my typical useage can be found in the original post so I won’t repeat those here. Needless to say, I am probably a fairly atypical user and certainly on the higher end of useage.
As mentioned last time, I installed David from the Blackberry Appstore so I could monitor my data useage. In the week that has passed my average has been around just over 10 megabytes of data a day. So this would average out to just over 300-320 megabytes for the month.
A quick peek on MTN and Vodacom’s websites to see how much it would cost for 300 Meg per month. Vodacom has a data useage calculator tool here. I entered 300 Meg and this is the very helpful response I got back :
So back to the 3 easy steps to see if I could get a different answer. Tried a few other options, same result. Vodacom clearly doesn’t want me to buy 300Meg a month. I browsed around the site but still couldn’t find the price. How hard is it to tell your customers what options there are and how much they would be ? I did find the Blackberry BIS service price which was R59 a month (prepaid). (No link sorry, their website seems to produce session specific links so had to remove it). Try www.vodacom.co.za and let me know if you find the data prices quicker than I did.
MTN was a little easier. I quickly found their data options and an “Extended Data 350” option which gave the required data amount for R209 a month. That though i then discovered was a complete contract not a bolt on to an existing contract. They have a 300Meg option for the grand price of R149 a month. Not too bad and not too hard to find.
So with some very poor maths and mixing and matching between service providers, it would seem that if I was paying for my data useage on the optimum data contract would cost me R149 a month rather than the Blackberry cost of R59 a month, an additional monthly cost of R90.
Is it any wonder then that people, and particularly teens are going for the Blackberry option? They generally like to use Facebook, Mxit, and are increasingly discovering the joys of a service guaranteed messenger in Blackberry messenger.
I fully expect Blackberry to continue to grow from strength to strength, and really hope that the other providers come out with some kind of competitive option. Increasingly other phones are coming bundled with a small data package, but, 30 Meg of data on an Android device (Bundle with SE X10 Mini) really doesn’t cut it, and can easily be used in an hour at the park.
In summary then, people often ask how good a deal is the Blackberry with unlimited data? Extremely good value for money is the short answer.
Process control / automation control systems /SCADA Security rootkit (Stuxnet) #in
Posted on August 10, 2010Having done a fair amount of work in the area of process control systems, and the design/implementation of control frameworks and minimum standards for these environments in the last few years, I am always interested in reading up on issues and threats being identified in this area.
My experiences have always been that the clients we have dealt with are relatively immature in their dealing with these environments (from an information security point of view) and have been reluctant to acknowledge the threats and take the necessary steps to protect themselves. They are reluctant to even carry out the basics such as patch management and installation of anti-virus, often pressured by the solution vendors not to.
I noticed a short while back that there was some noise of a new “virus” that targeted WinCC, at the time I read about it briefly and was interested to see that it targeted one specific environment and appeared from the comments to have been designed to attack one specific environment.
Details that are emerging now seem to indicate something altogether different. This virus not only targets on specific environment, but is also a security rootkit. It targets Siemens Step7 and WinCC. Step7 is used to program the Programmable Logic Controllers (PLCs) of the Simatic S7 family.
In an updated blog post found here, Symantec explain in a bit more detail the seriousness of what Stuxnet is and what it does :
“Stuxnet has the ability to take advantage of the programming software to also upload its own code to the PLC in an industrial control system that is typically monitored by SCADA systems. In addition, Stuxnet then hides these code blocks, so when a programmer using an infected machine tries to view all of the code blocks on a PLC, they will not see the code injected by Stuxnet. Thus, Stuxnet isn’t just a rootkit that hides itself on Windows, but is the first publicly known rootkit that is able to hide injected code located on a PLC.
In particular, Stuxnet hooks the programming software, which means that when someone uses the software to view code blocks on the PLC, the injected blocks are nowhere to be found. This is done by hooking enumeration, read, and write functions so that you can’t accidentally overwrite the hidden blocks as well.
Stuxnet contains 70 encrypted code blocks that appear to replace some “foundation routines” that take care of simple yet very common tasks, such as comparing file times and others that are custom code and data blocks. Before some of these blocks are uploaded to the PLC, they are customized depending on the PLC.”
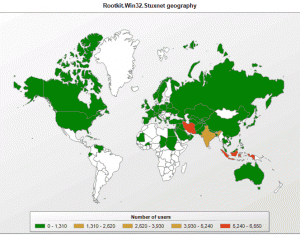
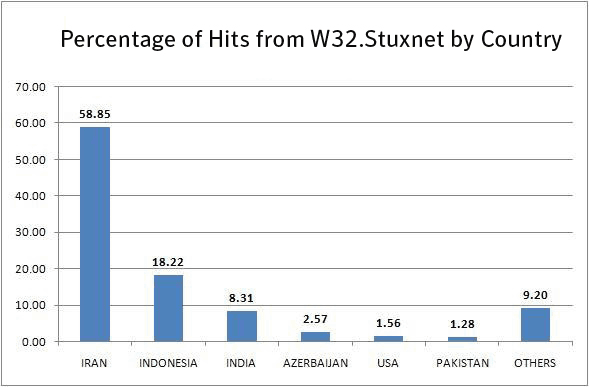
Two infographics have been shown in various places (Source : app Symantec), that show the distribution of the worm globally. This is not a localised phenomena that affects just one place in the world.
Iran, Indonesia and India are the areas most widely hit.
This virus is not just some theoretical proof of concept. In reading through some of the forums I came across this post, which could just as easily have originated from a South African organisation as a foreign one :
“Hi, currently I am in Iran, xxxx commisioning of our project for steel making plant.
We have this virus everywhere here, on WinCC server, clients and so on.
This virus was probably transfered from some USB stick from customer.
In this time I downloading Simatic patch and antivirus software from links above.
I am sure, that I have had this virus minimal one month ago in my project backups too.
So tomorow I try remove this virus and i will inform you. ”
From this it is clear that the environment they are in at least follows the basics of keeping the process control network separate from the organisations administration network and the Internet. This virus is smart, smart enough to know the target environment and run across multiple attack vectors. At very least, this virus is infecting USB memory sticks to get itself across to the process control environment. It is then infecting windows computers through open shares (and other vectors) and then attaching itself to the .DLLs on the WinCC machines and injecting itself into the S7 PLC’s, then modifying code on the PLCs to prevent it’s detection. This is serious stuff and introduces a few degrees more complexity than has been seen before in a worm targeting these sensitive devices.
If that wasn’t bad enough, once this virus has acquired targets, it is then reporting information back to it’s Command and Control centre, and also appears to have the ability to receive remote commands and execute them, as well as download further software from the command centre.
If you run a process control environment / SCADA / PLC’s then you should be concerned. IT security threat to the environment is no longer a theoretical or remote one. It is real, and you could be attacked, if you have not already been. It is important that you have the right governance and processes in place to provide you with both technical and procedural protection against attacks.
Has anyone heard of any infections here in South Africa?
Justin
Further reading:
Stuxnet introduces the first known rootkit for industrial control systems
http://www.symantec.com/connect/blogs/stuxnet-introduces-first-known-rootkit-scada-devices
Findings from the field : Stuxnet and Siemens
http://findingsfromthefield.com/?p=480
The Stuxnet worm and options for remediation : Download PDF from Industrial Defender here or get it from http://www.industrialdefender.com
Blackberry Data useage numbers in SA using DAVID #in
Posted on August 08, 2010I have been curious about Blackberry data useage for a while. The Blackberry contracts (BIS/BES) are around R65/month and include unlimited data for on-device browsing, email, IM, etc. I do a fair amount of browsing on my Blackberry (rather than my Nokia) largely because of the data. I have a small (30 Meg) data bundle on the Nokia and I regularly go over the limit. Not difficult to do given that some web pages (even on the mobile device) take a few hundred K, making it every easy to use a Meg or two reading just a few sites.
The other factor is that Blackberry is said to use a fair degree of compression through the use of their own data proxies and their own services. So how much value for money do I really get out of the Blackberry service?
I looked around for a tool to monitor the useage, and came across a few, but only one seemed as though it would be up to the task, so I downloaded “David” from the blackberry appstore. It is a 60 day trial version, but is more than adequate for monitoring a few days useage.
After 2 days, here is how it’s looking :
Two days useage +- 18 Meg (and after the 1st day it was around 9 Meg).
That includes Twitter, Facebook, Linked In, downloading some apps, browsing the net, BB Messenger etc. I am really impressed with the relatively low data useage given my patterns of useage. Anyhow, some very quick sums and it would be around 270 megabytes of data per month. For the price paid for the BIS/BES useage, that is really good value for money.
I’m probably an outlier on useage, though perhaps not in the top 2% of users. Still, for anybody looking to make decent useage of their mobile device and not to have to worry about crazy high bills, the Blackberry with “uncapped” data useage is a really good deal. BB Messenger also works a good deal better than MXit, they way its integrated into the device and has message delivery and read statuses. No more messages lost in the ether.
I’m interested in hearing about other people’s useage patterns and their thoughts on the Blackberry data bundle and value for money.
Feedback on ISACA KZN chapter meeting control frameworks presentation
Posted on August 07, 2010On Thursday evening (5th August) I presented at the ISACA KZN Chapter meeting. As Chapter coordinator I have the privilege of finding speakers and venues, and from time to time an arranged speaker has other commitments and so is unable to make the presentation. I always try and keep a “backup” presentation of my own and this time around it was my (our) “Tale of two cities – or control frameworks” presentation that was first presented at the IT Web security summit earlier in the year. This time I did the presentation without the assistance of my colleague from Jhb, David Volschenk, as he had other work commitments which prevented him traveling to Durban for the day.
It IT Web we had 45m for the presentation and Q&A so where fairly time constrained and did not have much time at all for discussion or questions. At the Chapter meeting we had much more time to go through the presentation at a leisurely place, have discussion around certain aspects and make it a much more interaction (and fun) session.
There were about 20 people present, representing the consulting firms (EY, PKF, Deloitte), public sector and private sector.
Off the top of my head (I was presenting rather than taking notes 🙂 the main areas of discussion were around :
- Getting executive buy in for the project
- Getting adequate funding
- Instilling change in an organisation where the maturity level is low and the corporate culture is such that the environment is generally poorly controlled
- What the drivers are for the implementation of a control framework, and particularly King 3 and how it is changing perspectives (creating the fire)
- The implications of King 3, and how they will drive change from the top (rather then it being left to middle management to drive failed projects)
- The apparent lack of understanding of King 3 on the part of directors, and how negative statements having to be made in the Annual Financials with respect to King 3 compliance could affect their reputations and those of the organisations they represent (or what happens if they “lie” and put in statements of compliance when they aren’t compliant). Company directors really do need to start taking notice of this.
- The implementation of control frameworks is a long term process, not a quick fix. Deciding 6 months ahead of the King 3 implementation deadline that the organisation needs to be compliant may be an impossible task
In “off the record” discussions after the presentation a number of consultants wanted to know if the failed company (Company B) was actually Company XYZ or Company ABC. The answer each time was know, it wasn’t that company, Company B was a combination of failed projects. That said, the names of companies mentioned by the other parties in each case also were not one of the companies involved in the combined “Company B”. It seems there are a lot of failed control framework and security framework implementations out there.
I really enjoyed the presentation and the discussions that went with it. Thanks to all who attended for your attendance and participation. If you are interested in having further discussions around this, or have me meet with your directors to discuss further, please contact me. j-j (at) worldonline (dot) co (dot) za or on Twitter.
Thanks to Ernst & Young for hosting the chapter meeting.
See you next time at PKF.
Justin
You can find a copy of the presentation in the original article or directly here. More on King 3 here. And get a copy of the King 3 report from the IOD website.

What people say
Close block